Suppress network noise from your smart TV with pfSense
February 9, 2018
Like millions of other folks, I have a smart TV,
or simply a tiny android box that plays Youtube music and Amazon Prime videos.
I also like to run pfSense firewall, with pretty much
out-of-the-box setup.
While checking firewall logs, and reviewing the usual scans for open ports 23/22 on my network,
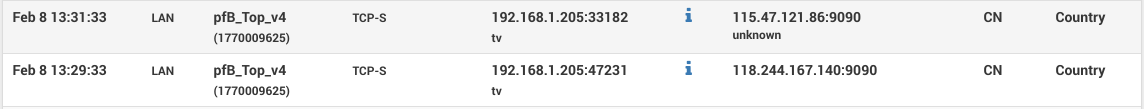
I decided to start blocking certain geo-locations. That's when I noticed my smart TV sending data
to two IPs in China, about every other minute.
Launching adb server, android shell and few minutes later -- the app responsible for those pings is
com.waxrain.airplaydmr2,
one of only 3 custom apps installed on the device.
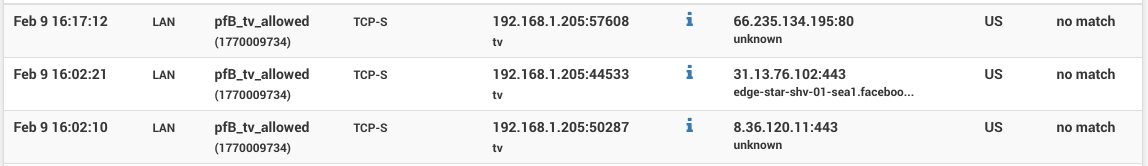
This got me curious of what other traffic this smart TV is leaking. Among the
usual Nvidia telemetry (even though it was explicitly disabled in the OS setttings),
there is chatter to Adobe, Facebook and a bit of others.
With pfSense however, we can easily quiet this chatter down.
0. Strategy
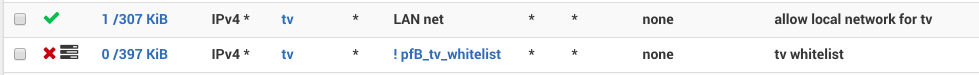
First, we need to decide which traffic we care about. I only care about youtube and amazon at this point, and while those two also query a ton of telemetry we'll just have to take the bad with the good here. But outside of those two services, the smart TV should be completely silent and invisible to the outside world. In order to block other traffic, we will create a pfBlockerNG alias to isolate google, amazon, and akamai (content delivery service for amazon video) using ASNs. Upon alias update, pfBlockerNG will resolve those ASNs to IP addresses that we can reference in firewall rules.1. pfBlockerNG alias
In pfSense, navigate to Firewall / pfBlockerNG / IPv4 and click Add. Now pick a cool alias name (such as tv_whitelist), set List Action: Alias Native, which means pfBlockerNG will only create an alias (in Firewall / Aliases / URLs), and won't add actual firewall rules. Further down in IPv4 Custom List tab, check Enable Domain/AS and paste following ASNs into Custom Address(es).AS15169 AS36040 AS22577 AS36561 AS14618 AS16509 AS11344 AS19047 AS7224 AS6432 AS16550 AS62785 AS58588 AS393560 AS393234 AS36183 AS35994 AS35993 AS32787 AS30675 AS23455 AS23454 AS22207 AS20189 AS18717 AS18680 AS17334 AS16702 AS16625 AS12222Once alias is saved, run pfBlockerNG update and reload steps on Firewall / pfBlockerNG / Update page. The log should state that a few thousands of IPs have been added, about 19000 as of this writting.